Gumblar.cn is a website is listed to be suspicious and contains several exploit scripts and trojans that might harm and infect computers. Google marked it as not safe for browsing. I first encountered on a website that I am working on and seen how and where it infects the website. What the trojan did on the site is it embeds its encrypted scripts on .HTML, .JS and .PHP files. You can find the Javascript of the trojan on .HTML files prior to the <body> tag while it embeds itself on .JS files at the bottom most of the said script file. On .PHP files, it usually infects INDEX.PHP files and embeds itself either at the top or bottom of the file. I also found some infections on common .PHP files that are usually INCLUDEd as a constant file of the site. The current anti-virus that detects the said virus was AVAST Home Edition with Web Shield and Networking Shield ON.
Here’s what you will see if you will try to surf a site on Google Chrome that is infected by the trojan coming from the said site:
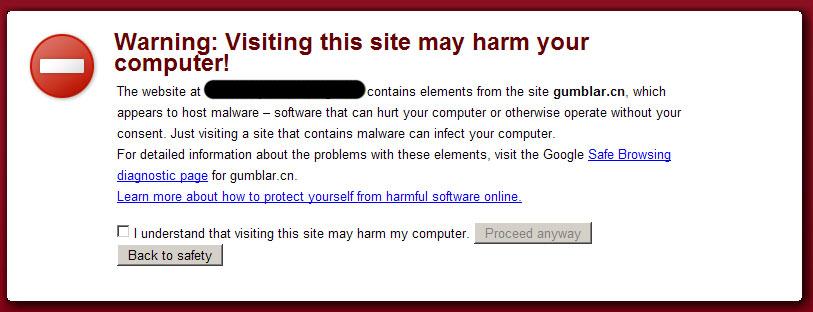
Now, how to remove it from your website? Well I found no reference on the net to remove it instantly so what I did is I removed the trojan scripts on each file (.JS, .HTML, INDEX.PHP) that I suspected for infection using Filezilla (FTP client program). For the WordPress infection, what I only did was I re-updated / upgraded the site to the latest version which causes the process to override existing files then remove the script from the WP-CONFIG.PHP file. This is the only file that is not overwritten by the said process that’s why I need to remove the trojan scripts manually.
As always, prevention is better than cure to avoid the pain of fixing the problems it cause to the site and to the owner. Here are some of my suggestions and recommendations I found from different web hosting sites regarding avoidance of hacking and malware infections on your site:
- Change the file attributes of the files that doesn’t require writing permissions. I usually set my files to 755 attributes (MOD 755)
- Update your antivirus virus database and enable or use network + web shield features at all times. Usually infection of websites starts from the local PC that uses to upload new files.
- Read this PHP Security fixes recommended by a web hosting company. It contains comprehensive tips on how to avoid PHP exploits and hacks. Read it carefully and apply it if it is possible.
If you have any better solutions out there or any recommendations on dealing on this kind of exploits/hacks, feel free to leave it here. I am sure that a lot of people will really highly appreciated the help that you can provide.

Hi i have made this script to detect and remove gumblar signatures here
http://digitalpbk.com/virus/gumblar-web-virus-manual-removal-free-tool
Never store your passwords digital or use some special programm like KeepPassSafe.
Because getting rid of this kind of malware is something you must prevent.
Filezilla is not safe. I use it but let the programm always ask for the password. I learned my lesson. It took me 3 full weeks to get clean for sure.
There’s a little bit more to Gumblar than that, but you summed up the damage it can do. Here’s what I’ve discovered:
Gumblar seems to be spread through various methods but even if you don’t visit the site that has the additional code injected into it, you can get it through other methods. I’ve read about it getting in with PDF files and Flash files (though I’m not sure about the accuracy on the latter but can see how it would be possible).
What this beast does is it infects your computer and uses your FTP program to infect your sites. It also sniffs packets going in and out of your computer to get additional FTP info, but if you use dreamweaver or filezilla or something like that, it will use the info you already have stored in your program. All the work is done on your computer, the downloading and changing of the file and reuploading. It just happens in the background.
From an IT standpoint, this thing is one of the biggest pains I’ve delt with because if you work with alot of sites (I work with over 200 which are stored and many more that aren’t) it’s time consuming to fix it.
Great info. How do I know if I have this virus?
I may be naive and I may be blasted as a “fanboy” but I fail to understand why anyone would use an OS that just doesn’t get security – even after 15 years of trying. Windows is basically flawed, until it gets a total makeover, I suggest using something stable. Linux, Unix or MacOS X.
These problems don’t happen there.
nice post kabayan….
[…] Here are a list of links related to the Gumblar trojan : Gumblar explode across the Web Beware of the Gumblar Worm PHP exploit on the loose 12 Facts about the Gumblar Exploit Removal and Prevention of Gumblar […]
Nice artticle !
If you suspect that your PC running windows is infected, also delete all temporary internet files.
Best regards,-A
I created a script yesterday for automatically removing the trojan from a website, and posted it on my blog. (Since I disinfected my site last night, it may still be reported as an attack site, but I requested a review by Google, so that should be done tomorrow – ignore the warning.)
http://www.danielansari.com/wordpress/2009/05/automatic-removal-of-gumblarmartuz-trojan/
Howdy…
I had this nasty guy on my site. I downloaded my entire site to a separate hard drive, then ran avast through the files. I found the infected code (posted below) and removed from each file from my C Panel, changed all PW’s. This was a tough ball to break indeed!
Good luck!
script language=javascript>